How quantum photonics is redefining secure communication in the age of quantum computing
We are standing at the brink of a digital paradigm shift. The relentless tide of technological progress is carrying us into the quantum age, a new era filled with both extraordinary promise and existential challenges. Quantum computing, once a subject of abstract theoretical speculation, is rapidly evolving into a practical reality, with the potential to revolutionize fields as diverse as materials science, artificial intelligence, and medicine. However, alongside its immense possibilities comes a profound threat to cybersecurity—one that could fundamentally compromise the encryption methods that secure our financial systems, personal data, and classified communications.
Today’s cryptographic security is built upon mathematical problems that are impossible to solve within a reasonable timeframe using classical computers. These intricate algorithms protect everything from bank transactions to state secrets. However, quantum computers, leveraging the bizarre yet powerful laws of quantum mechanics, have the potential to dismantle these defenses with ease. The computational complexity that has served as our digital shield is now at risk of collapse, leaving sensitive data vulnerable to quantum decryption techniques.
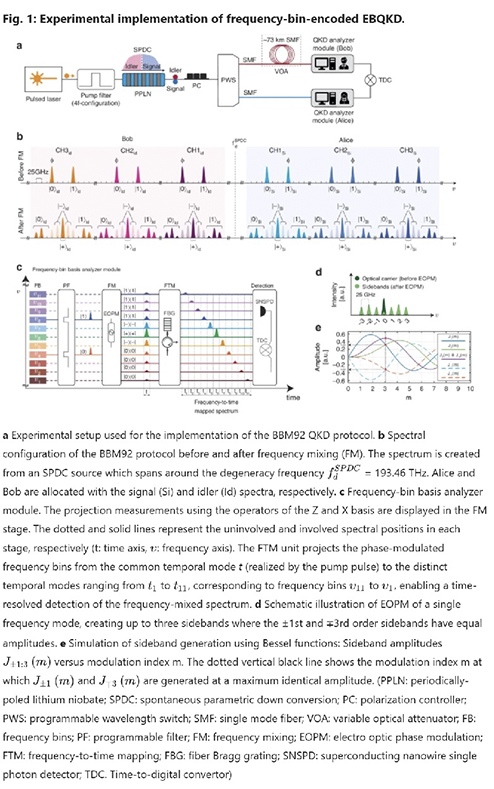
To address this looming crisis, researchers across the world are racing to develop quantum-secure networks—communication systems that use the fundamental properties of quantum mechanics to create encryption that is not just strong, but fundamentally unbreakable. Among those leading the charge are scientists at Leibniz University Hannover, who have pioneered a groundbreaking innovation in quantum key distribution (QKD). Their latest research, published in Light: Science & Applicationson January 16, 2025, introduces an advanced frequency-bin coding technique, a novel approach that replaces the traditional polarization-based quantum encryption with encoding information in different light frequencies—akin to using the “color” of light to secure data.
This seemingly subtle shift unlocks significant advantages. Frequency-bin coding not only enhances security but also simplifies hardware requirements, reduces costs, and improves scalability—all critical factors for the future deployment of real-world quantum networks. Instead of requiring multiple photon detectors and complex polarization systems, this method enables secure communication using a far more efficient, cost-effective approach. This work was supervised by Prof. Dr. Michael Kues as part of Dr. Anahita Khodadad Kashi’s research.
A Conversation with Dr. Anahita Khodadad Kashi
Could you illuminate your academic journey and the allure that drew you to quantum photonics?
“With a voice suffused with wonder, Dr. Kashi reflects, ‘The counterintuitive insight that quantum science provides—its ability to alter our common perception of reality—first attracted me. As a doctoral researcher in quantum photonics, I’ve been fascinated by the transformative potential of quantum mechanics to secure our everyday communications. My research centers on photonic quantum information processing and quantum-enhanced secure systems, focusing on scalable implementation of quantum key distribution protocols that harness entanglement—the non-classical, non-local correlations between photons. I also study photon statistics, bridging theoretical models with experimental implementations and how to transition research into meaningful applications. My research has been published in premier journals and presented at international accredited conferences.’”
What dire threat do quantum computers pose to conventional encryption, and what perils loom for data integrity?
“Dr. Kashi’s tone grows resolute: ‘Today’s communication security relies on computationally intractable mathematical problems that classical computers cannot solve within feasible timeframes due to their exponential complexity and massive energy needs. Yet, quantum computers and advanced quantum protocols relax this complexity considerably, unleashing a profound threat to the existing cryptographic shield. The danger? Exposed data from financial systems, medical records, and sensitive governmental secrets laid bare to the quantum decryption’s power.’”
What inspired you and Professor Dr. Michael Kues to pursue entanglement-based quantum key distribution via frequency-bin coding?
“Entanglement-based quantum key establishment holds the promise of redefining secure communications,” Dr. Kashi muses, her words alight with possibility. “Yet, its practical realization remains challenging as entanglement quality degrades with distance, hindering large-scale deployment. Compounding this, the growing hardware costs, complexity, and security risks as quantum networks expand pose a challenge to scalability. Despite the great achievements in the field, the lack of scalable solutions for global entanglement-based quantum key distribution networks encouraged us to leverage our profound expertise in frequency encoding, showcasing its capability to address the scalability issues.”
Could you elucidate frequency-bin coding and its role in bolstering quantum key distribution’s security?
“With poetic clarity, Dr. Kashi explains, ‘In photonic quantum networks, photons are our carriers of information. Frequency—the photon’s hue—becomes the degree-of-freedom for encoding and processing of quantum information. By exploiting frequency’s multimode nature, we can define arbitrary (but limited) number of ‘ frequency bins’ across the photon spectrum, using entanglement between the frequency bins to establish quantum channels for secure key exchange. Crucially, this aligns with cutting-edge telecommunications infrastructure, building on the state-of-the-art advancements. Our frequency-bin approach allocates multiple channels to users, amplifying key exchange rates without compromising security—unlike increasing the excitation power, inevitably accompanied by higher error rates. We’ve developed a dynamic, resource-efficient quantum key distribution network, reducing the need for multiple detectors and basis analyzers, enhancing the security by minimizing vulnerabilities to detection side attacks arising from dark counts and detection probability mismatches.’”
How does frequency as an encoding dimension outshine polarization in resisting environmental noise?
“Polarization is confined to two dimensions and is vulnerable to decoherence in fiber-optic systems,” Dr. Kashi notes. “Frequency, however, is compatible with standard fiber-optic telecommunication components, offers a multidimensional encoding capability, is inherently more resilient to noise. In addition, the naturally higher phase stability renders frequency more robust towards environmental fluctuations, positioning it as a promising candidate for long-distance, fiber-optic quantum communications.”
Could you describe the frequency-to-time transfer technique and its role in measuring quantum states with a single detector?
“Gracefully, she elaborates, ‘Quantum communication protocols, including QKD, rely on random projection measurements for security—typically requiring two detectors per basis, totaling four per user for two-dimensional encryption. This hardware overhead grows exponentially which hinders scalability and leads to increased vulnerability to detection-side attacks. Our frequency-to-time mapping technique is based on the use of dispersion-shifted fibers to create time-resolved replicas of the photon spectrum, enabling simultaneous detection of multiple projection states within a single pulse—using just one detector. This simplifies complexity, fortifies security, and unlocks scalable networks.’”
Your method dramatically reduces component costs. How does this enhance the feasibility and scalability of quantum networks?
“By requiring fewer detectors and analyzers, we achieve resource efficiency and boosted security,” Dr. Kashi affirms. “This cost reduction and relaxed complexity and hardware overhead unlocks scalability, making quantum networks viable for global adoption.”
How does adaptive frequency division multiplexing elevate key distribution rates and dynamically refine network performance?
“Adaptive frequency multiplexing allows us to define and allocate arbitrary (but limited) number of frequency channels within the available bandwidth, flexibly assigning them to users,” she explains. “This dynamically adjusts key exchange loads without sacrificing security, enabling simultaneous, secure key establishment across multiple channels.”
In what ways does your approach enable scalable, resource-optimized quantum networks supporting multiple users over vast distances?
“By needing just one detector and one basis analyzer per user—versus twelve and six, respectively, in alternative schemes using polarization—we minimize resources while leveraging dynamic multiplexing,” Dr. Kashi says. “This design supports multiple users and extends secure key distribution across large distances.”
What transformative applications do you envision for this technology in critical sectors like banking and healthcare?
“As quantum computers emerge, classical cryptography—built on mathematical hardness—will yield to quantum protocols,” Dr. Kashi predicts. “In healthcare, this ensures protection for patient data, preventing from unauthorized access. Banking and government sectors will benefit from quantum-enhanced computing for precise prediction of their customer behavioral patterns from vast datasets. Nevertheless, distributed quantum computing relies on maturing quantum communication technologies, including quantum repeaters and memories, which demand further research and investment.”
How might further exploration of nanophotonics and quantum optics enhance multidimensional quantum information coding?
“Nanophotonics and efficient on-chip integration can revolutionize quantum communications,” she envisions. “By reducing transmission losses in nanostructured waveguides, we can boost key rates. In quantum repeaters based on nanophotonic designs, the capability of quantum memories for efficient storage and retrieval of quantum states could enhance, bringing us closer to practical, scalable systems.”
What lies ahead in your research, and what breakthroughs do you anticipate for ultra-secure quantum communication?
“Looking forward, extending secure key distribution over longer distances and among multiple users is our next goal,” Dr. Kashi says.
As the quantum revolution unfolds, future research will be conducted in Prof. Dr. Michael Kues research group and in their laboratory, where Dr. Kashi is a post doc researcher.